
CyberAI SecOps
(On-Prem, Agentic AI for SOC)
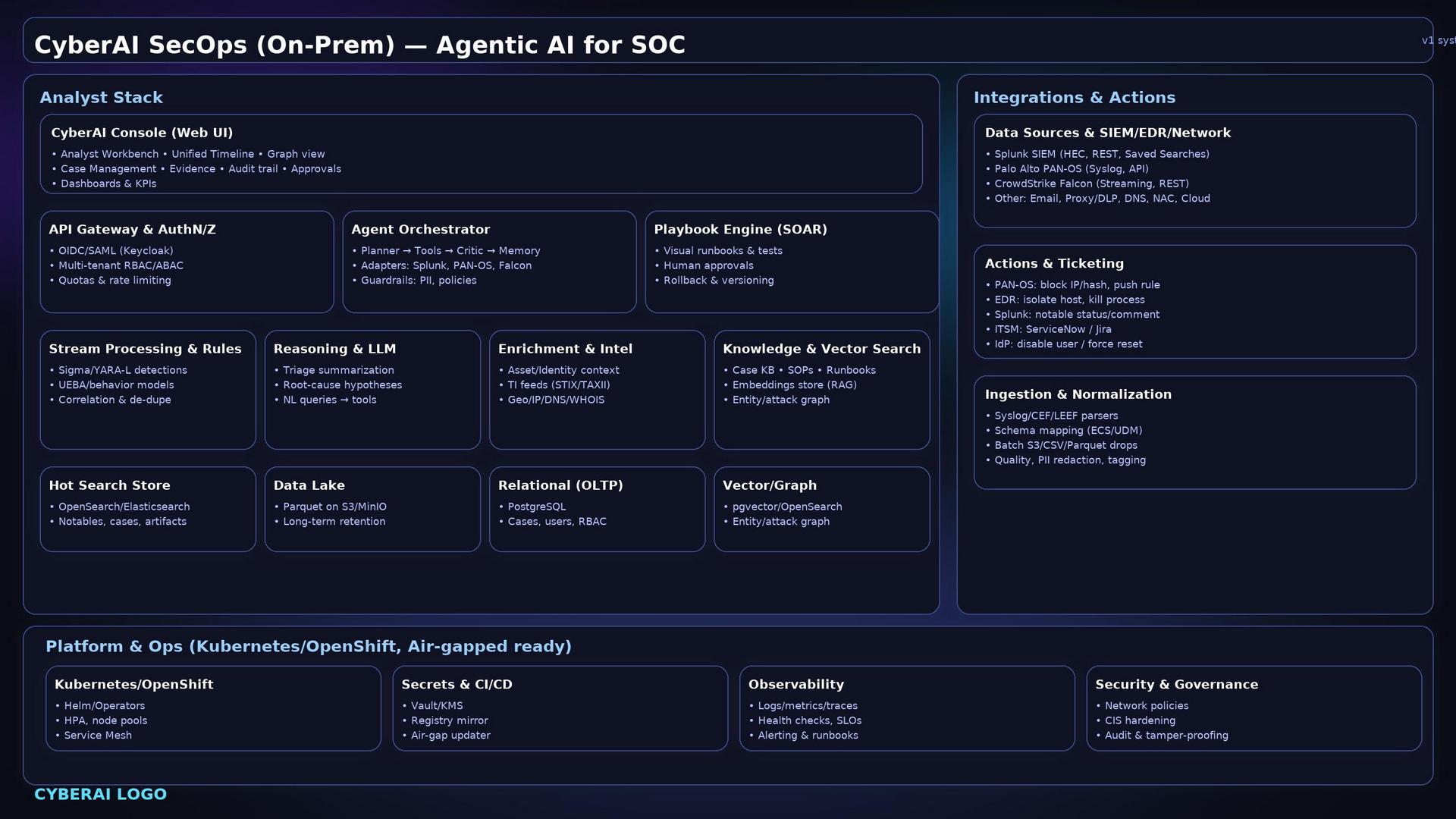
Control Plane
- API Gateway & AuthN/Z: OIDC/SAML (e.g., Keycloak), multi-tenant RBAC/ABAC, quotas/rate-limit.
- Agent Orchestrator: planner → tools → critic → memory loop; adapters (MCP/tooling) for Splunk, PAN-OS, CrowdStrike, etc.; policy guardrails (PII, change windows, approval checks).
- Playbook Engine (SOAR): visual runbooks, tests/versioning, human-in-the-loop gates, rollback.
Detection, Reasoning & Enrichment
- Stream Processing & Rules: Sigma/YARA-L, correlation & dedupe, UEBA/behavioral models.
- LLM Services: triage summaries, root-cause hypotheses, natural-language to actionable tool queries.
- Enrichment: asset/identity context (CMDB/IdP), STIX/TAXII intel, Geo/IP/DNS/WHOIS.
- Knowledge & Vector Search: SOPs/runbooks/case KB + embeddings (RAG), entity/attack graph.
Storage & Indexes
- Hot search: OpenSearch/Elasticsearch for notables, cases, artifacts.
- Data lake: Parquet on S3/MinIO for long-term retention.
- Relational (OLTP): PostgreSQL for cases, users, RBAC, configs.
- Vector/Graph: pgvector/OpenSearch kNN + entity/relationship graph.
Integrations (on the right side of the diagram)
- Ingest:
- Splunk SIEM via HEC/Saved Searches/REST.
- Palo Alto PAN-OS via Syslog + XML/REST.
- CrowdStrike Falcon via Streaming API/REST.
- Others: Email, Proxy/DLP, DNS, NAC, EDRs, Cloud logs.
- Normalize to ECS/UDM; batch
S3/CSV/Parquet drops; quality checks & PII redaction.
- Actuation:
- PAN-OS: push rule/block IP/hash.
- EDR: isolate/kil l process.
- Splunk: update notable status/comment.
- ITSM (ServiceNow/Jira): auto-ticket & enrich.
- IdP (Okta/AD/M365): disable/force reset.
Platform & Ops (on-prem / air-gapped ready)
- Kubernetes/OpenShift (operators/Helm), HPA, service mesh.
- Secrets & supply chain: Vault/KMS, private registry mirror, air-gap updater.
- Observability: logs/metrics/traces, SLOs, health checks, alerting.
- Security & governance: network policies, CIS hardening, immutable/auditable trails.
Typical alert-to-action flow (agentic)
- Ingest alert from Splunk or syslog (PAN-OS) → normalized → quality checks.
- Detect/Correlate with rules + UEBA; dedupe & group into incidents.
- Reason: LLM summarizes, proposes hypotheses & next best actions; planner picks tools.
- Enrich: pull context (asset, identity, TI feeds), fetch raw evidence (Splunk query tool).
- Decide: orchestrator evaluates policy guardrails; if sensitive, request analyst approval.
- Act: run playbook steps (e.g., PAN-OS block, EDR isolate, create ITSM ticket).
- Document: case updated with evidence, actions, approvals; KPIs/dashboards refreshed.
Deployment notes (on-prem realities)
- Air-gap: mirror container registry; offline model/KB updates; deterministic build pipeline.
- Data residency: S3-compatible storage (MinIO) with lifecycle policies; per-tenant encryption keys.
- Scale: split hot/warm/cold tiers; queue (Kafka/RabbitMQ) between ingest and processors; shard OpenSearch.
- Models: serve locally (e.g., vLLM/NVIDIA Triton) with policy-filtered prompts and response audits.
